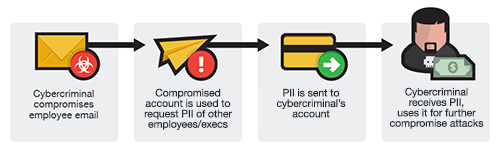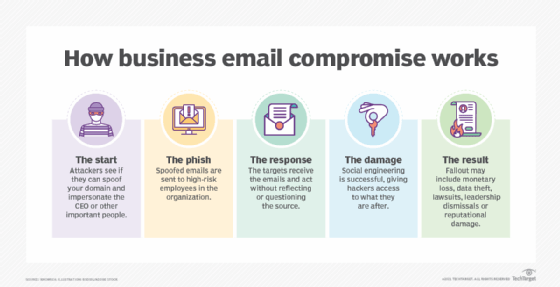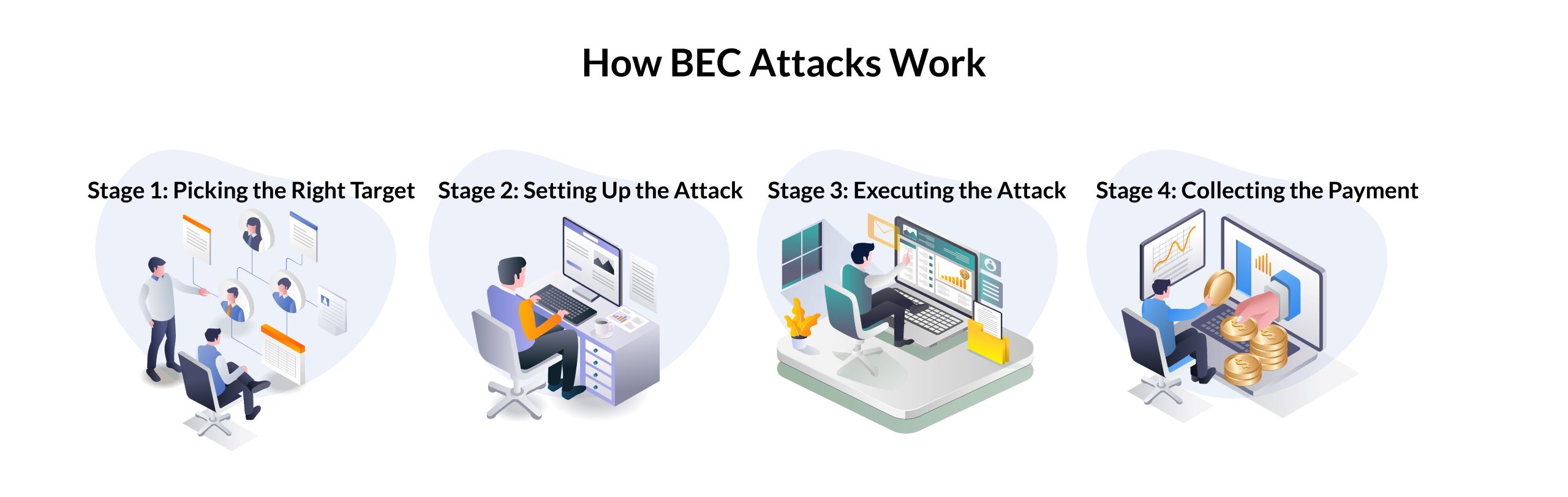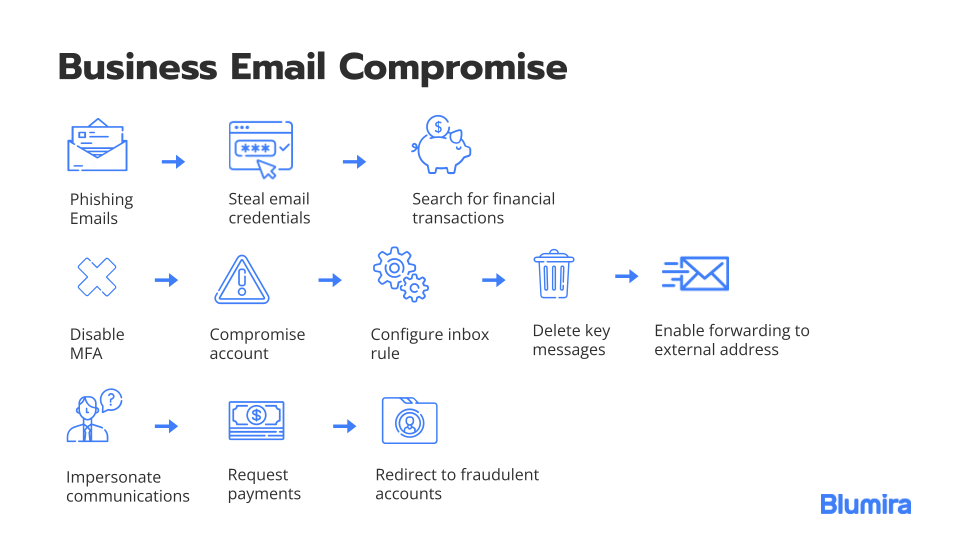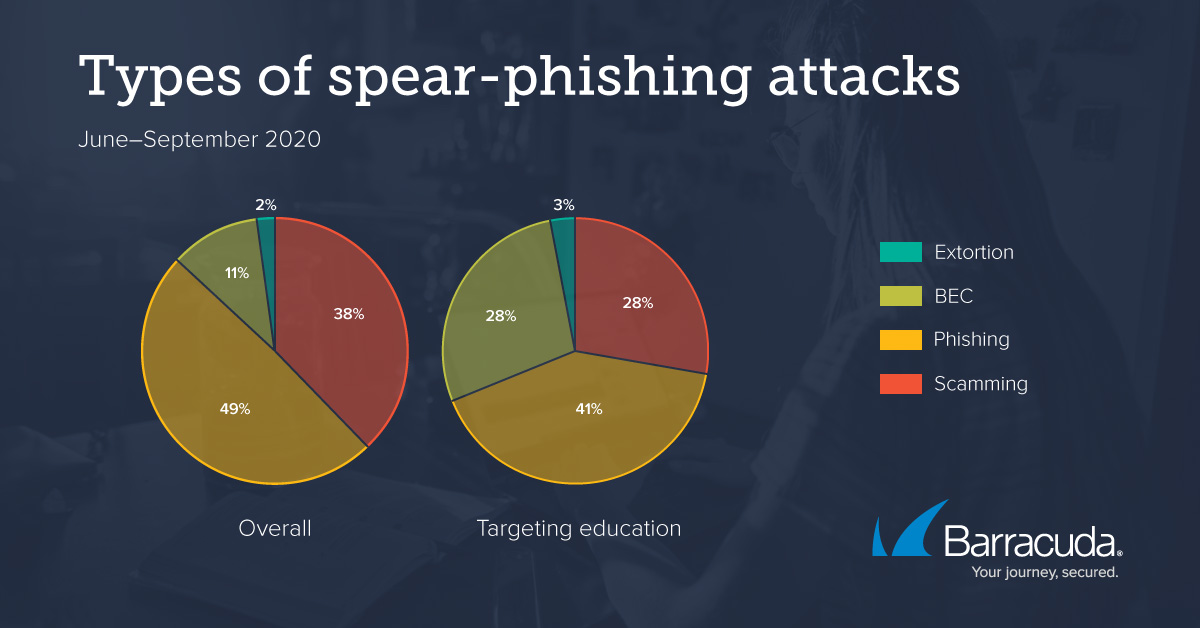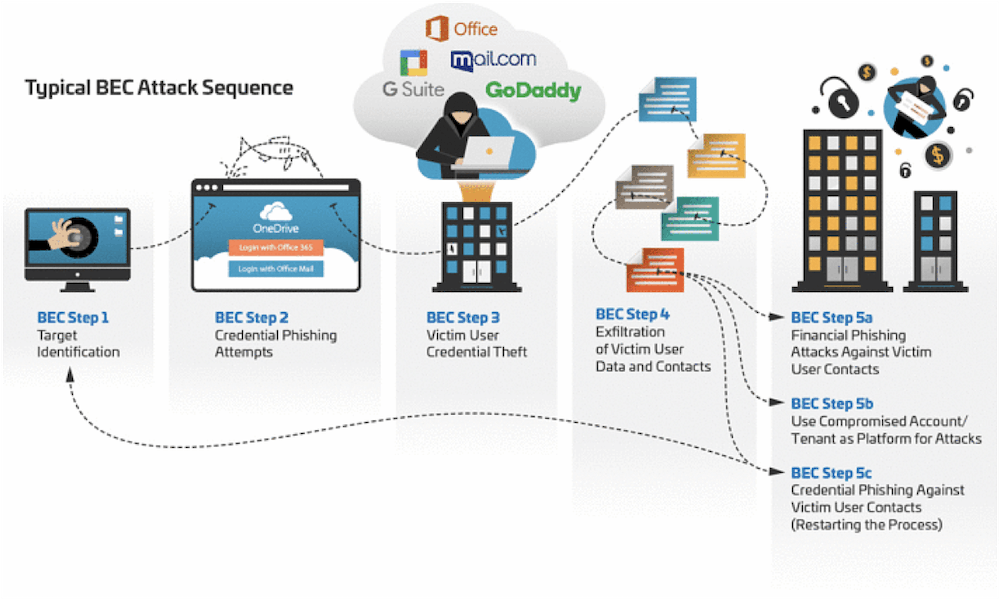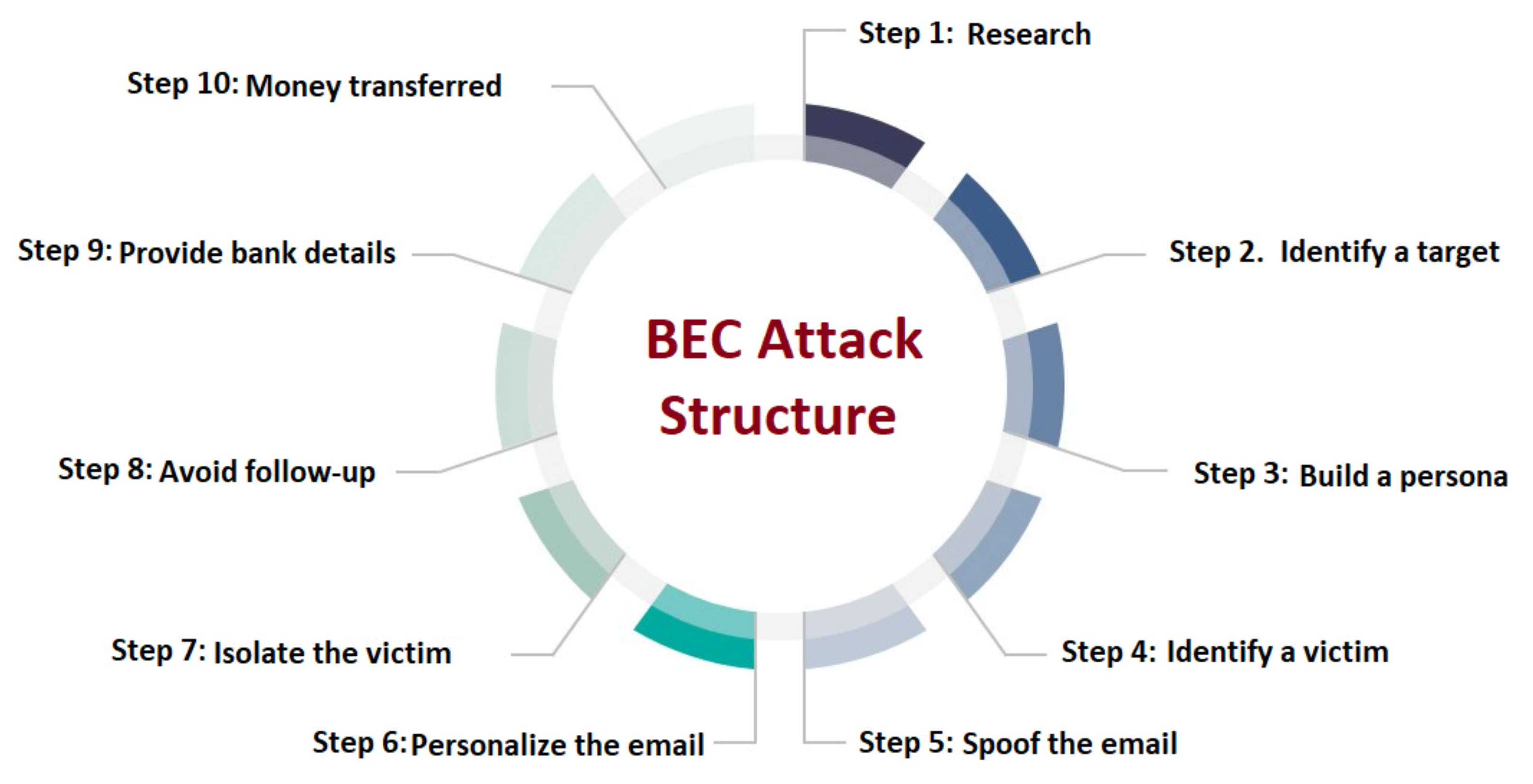
Electronics | Free Full-Text | Business Email Compromise Phishing Detection Based on Machine Learning: A Systematic Literature Review

Billion-Dollar Scams: The Numbers Behind Business Email Compromise - Nachrichten zum Thema Sicherheit - Trend Micro DE

How to Spot & Protect Against Business Email Compromise (BEC) Attacks - Hashed Out by The SSL Store™



.png)